🔓Setting Permissions
Learn how to configure permissions on your new QBCore server!
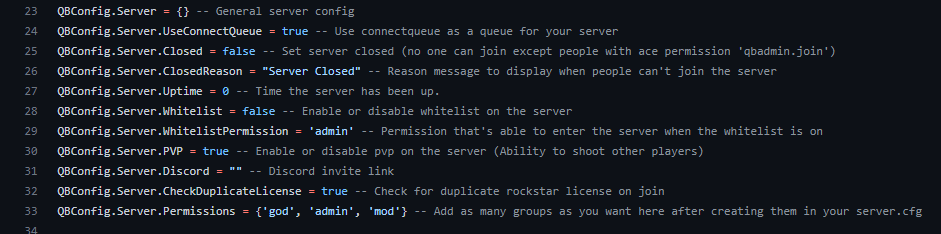
Server Config
## Permissions ##
add_ace group.admin command allow # allow all commands
{{addPrincipalsMaster}} # This is the way txAdmin assigns permissions to the server owner
# Resources
add_ace resource.qb-core command allow # Allow qb-core to execute commands
# Gods
add_ace qbcore.god command allow # Allow all commands
# Inheritance
add_principal qbcore.god group.admin # Allow gods access to the main admin group used to get all default permissions
add_principal qbcore.god qbcore.admin # Allow gods access to admin commands
add_principal qbcore.admin qbcore.mod # Allow admins access to mod commands Different types of identifiers

Setting users permissions in the server
Allowing commands to specific permissions
Last updated
Was this helpful?
